This post outlines the options that exist for connecting your on-premise network to AZURE. Following are the three options, This post explains configuration steps that required for setting up Site-to-Site Virtual Private Network.
- Site-to-Site Virtual Private Network
- Point-to-Site Virtual Private Network
- Express Route
Why do we need to extend On-Premise network?
Reason 1, If Your organization policies doesn’t allow to move some of your on-premise VMs to cloud but still want to talk with AZURE Cloud and leverage some services.
Reason 2 , You may want to use AZURE as disaster recovery site. For example you can replicate entire infrastructure setup that you have on-premise to AZURE VMs and fail over to it in the event of disaster.
Reason 3, If you want an high-speed secure WAN between on-premise and cloud without going over public net work.
Site-to-Site Virtual Private Network
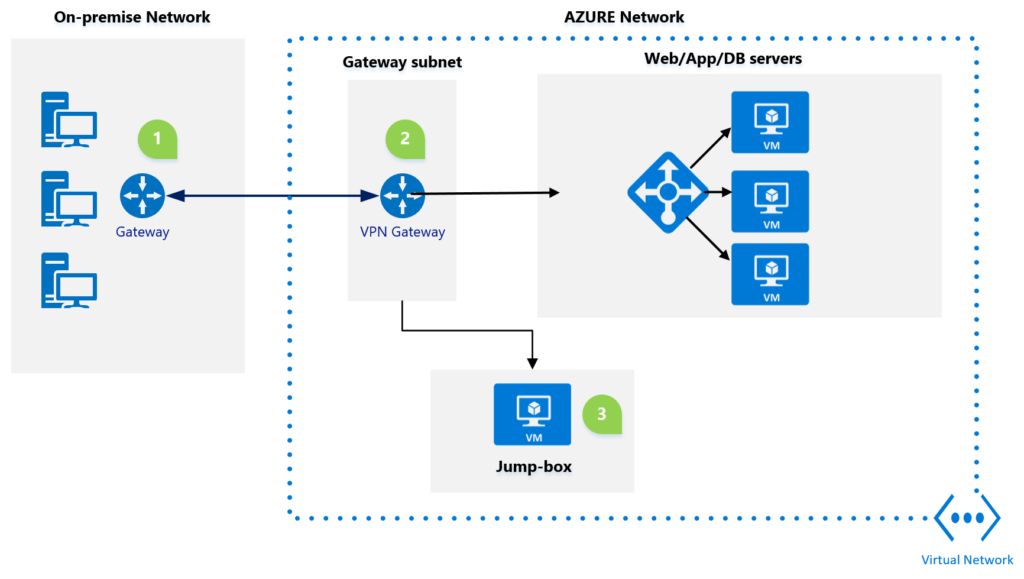
- The site-to-site VPN uses industry standad IneternetProtocolSecurity/Internet Key Exchange v2 protocol, if you use this standard then you dont have to purchase special VPN hardware for your on-premises environment.
- Connection goes from On-premise network to AZURE Virtual Network. Azure Virtual Network is boundary where you have VPN Gateway that needs to be placed on it’s own subnet virtual network.
- The jump box configuration allows user to manage virtual machines in azure network without exposing a public-end point.
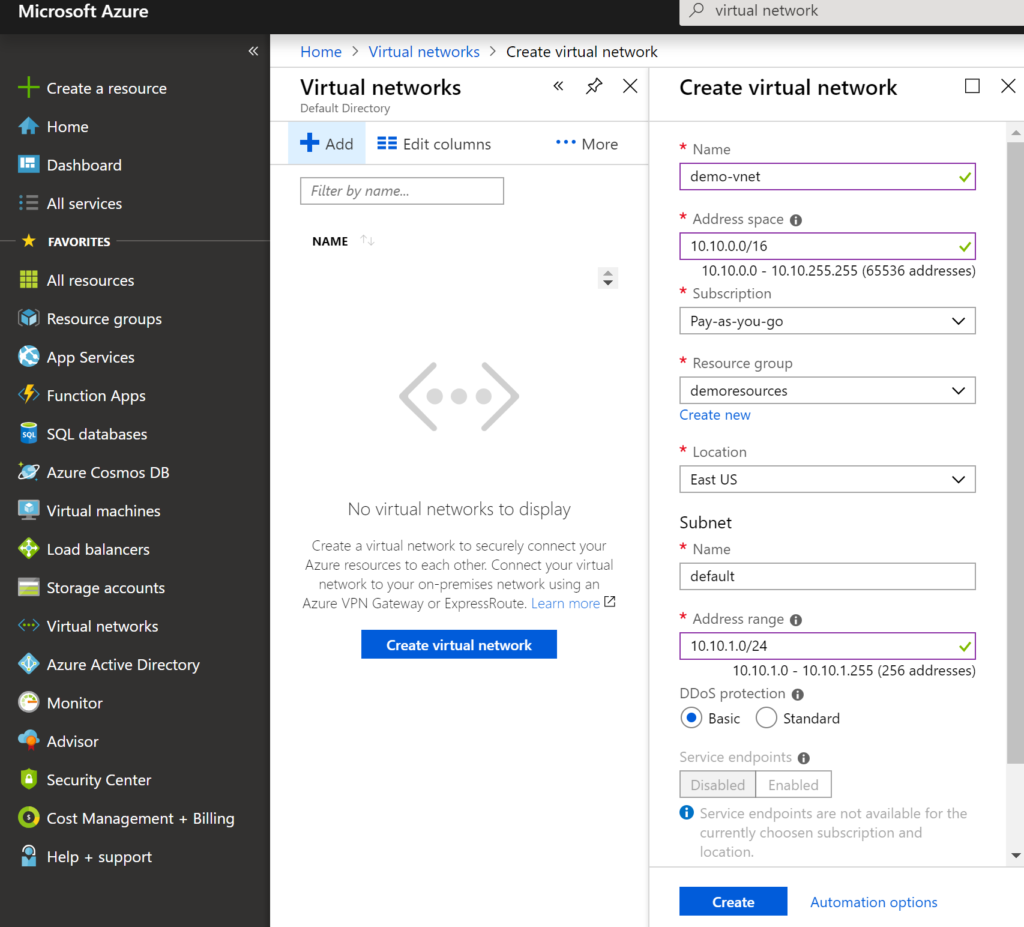
Step 1 – Create a Virtual Network in AZURE
Virtual Network is set of one or more IPv4 address spaces. Virtual Network address space can be break-down into one or more sub-nets. The routing among sub-nets is handled by AZURE where as in on-premise you use layer 3 switch or router. In this case IP addresses in sub-net are private.
You can create address space and initial subnet in azure by searching virtual network in azure portal and say create as shown in above screen.
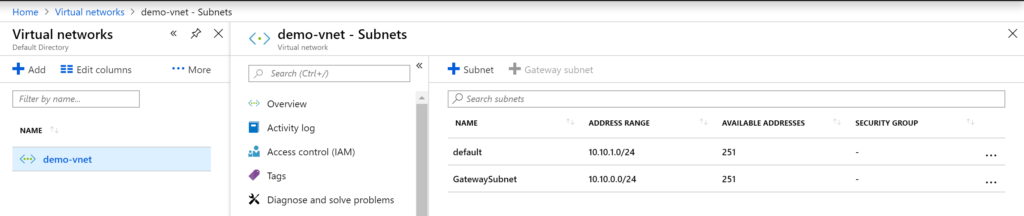
Add a Gateway subnet to above virtual network, you must have Gateway subnet in azure to communicate with on-premise network
Step 2 – Deploy VPN Gateway in AZURE
AZURE VPN Gateway uses different connection options to connect to on-premises network gateway VPN. You can also use AZURE VPN Gateway to connect to another Virtual Network(V-net to V-net) in AZURE. AZURE VPN Gateway can be used in express-route and point-to-site connection options.
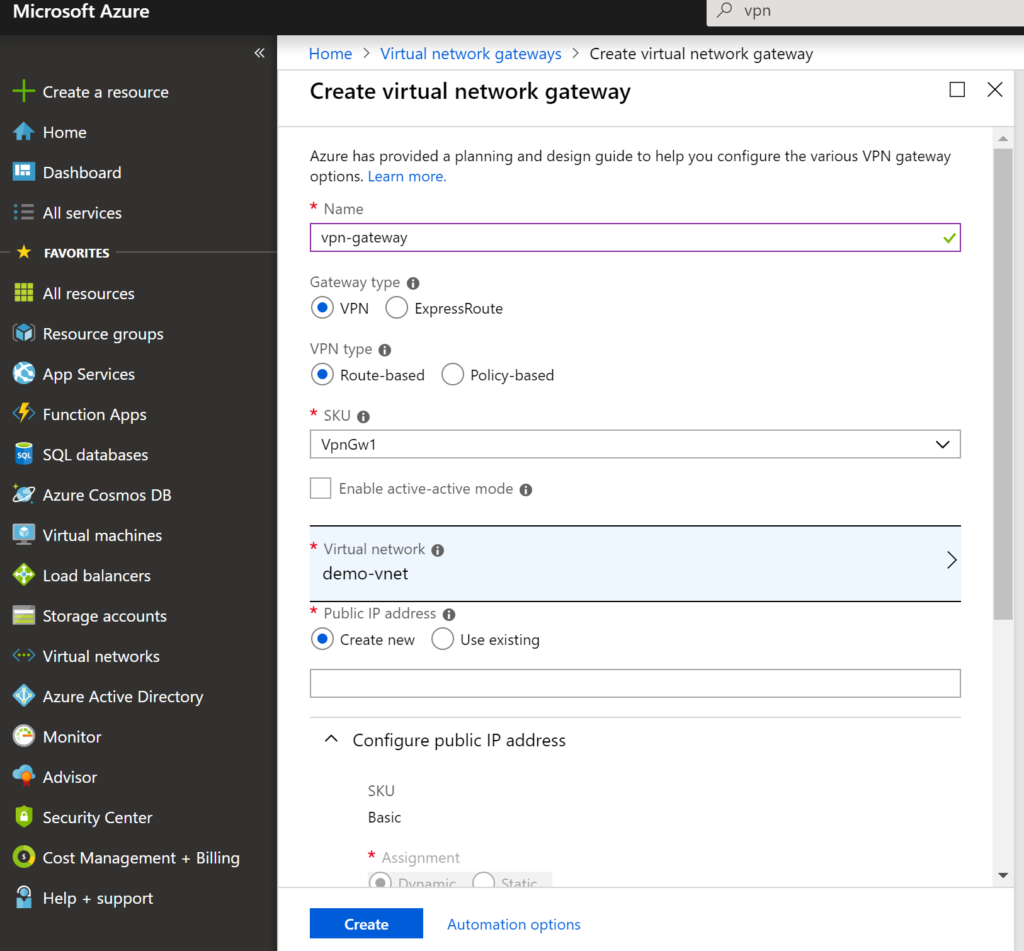
give a name to your vpn gateway, choose gateway type as VPN and VPN type as Route-based . There is a charge involved in connecting AZURE VPN gateway to on-premise network in the form SKUs, following table shows the each option with price
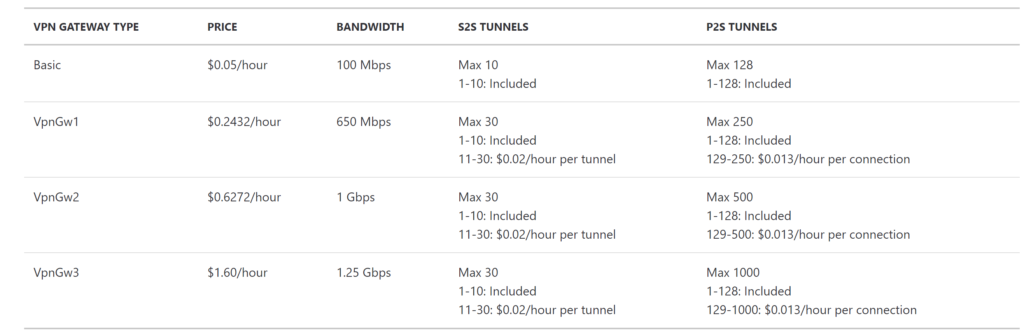
select the SKU option that suites your requirement. Next you need select the virtual network and say create. The VPN Gateway deployment may take an hour or so to make it available for the connecting to on-premise.
Step 3 – On-Premises configuration
This involves creating a local network gateway in AZURE which represents on-premise VPN device. If you don’t want to use your production equipment during the configuration then you can use Routing and Remote accessing service in windows server. more on this can be read here
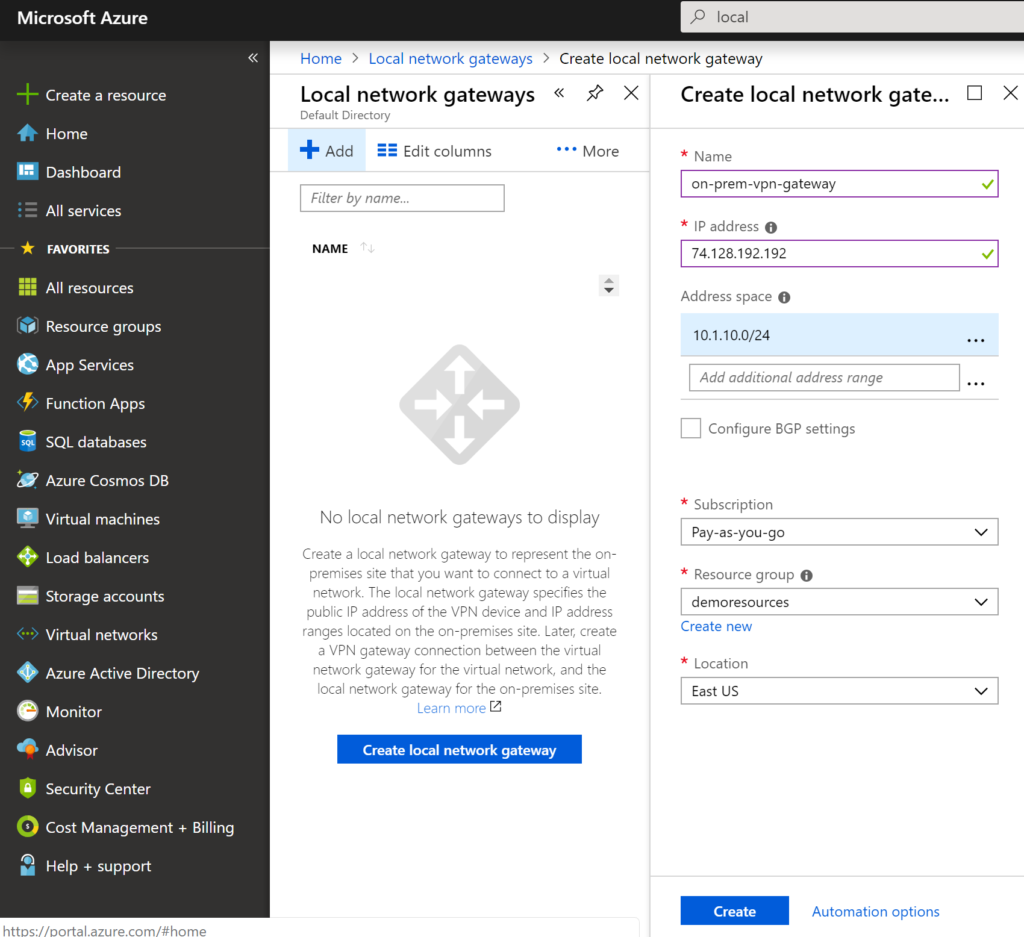
Give a name to local VPN Gateway, IP address is public one i.e. from on-premise server and on-premise Address space and say create.
On RRAS (Routing and Remote accessing server), create a network interface
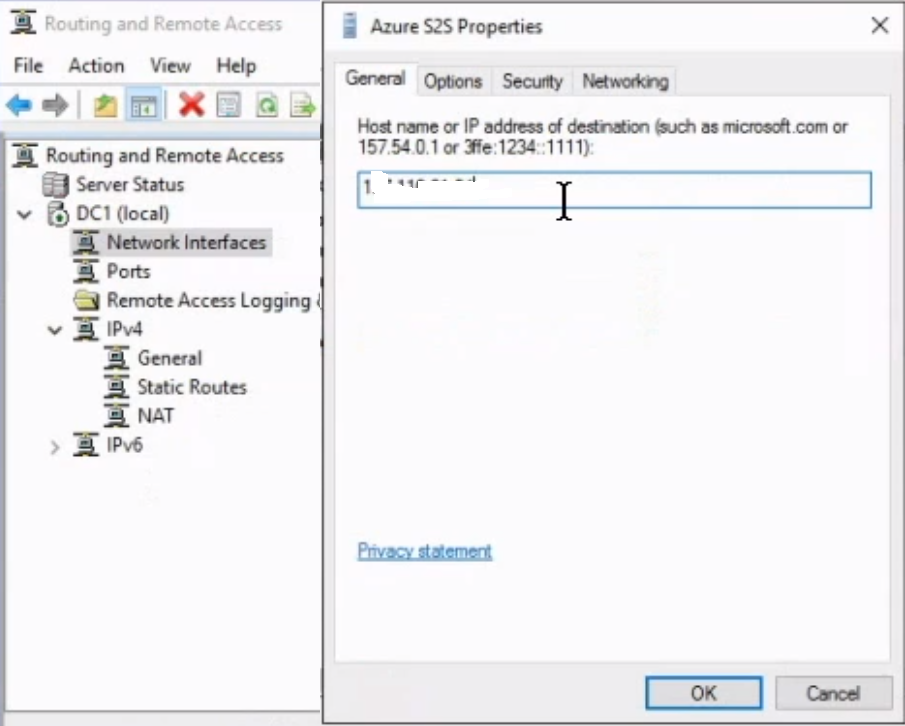
Specify AZURE VPN Gateway public IP address in network interface and on security tab select Type of VPN as IKEv2 and enter shared access key for authentication
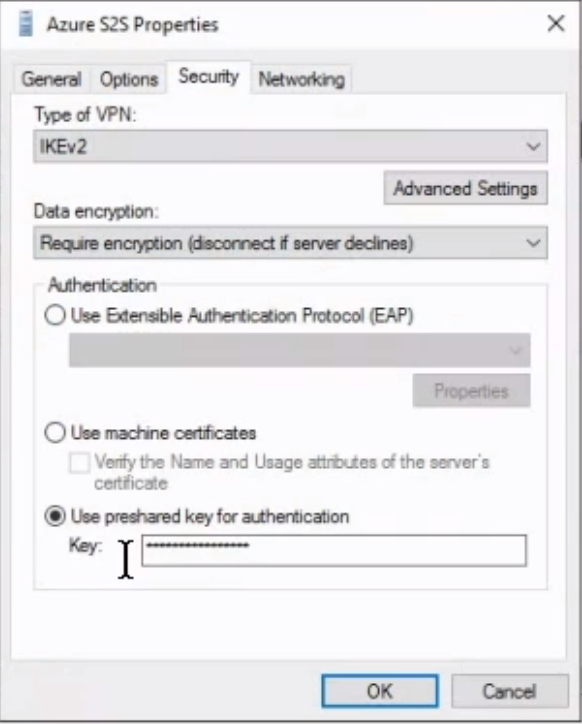
There is one last step to establish the connection with Premise network
Step 4 – Establish the Connection
Navigate to local network gateway in AZURE and add a connection as shown in following screen
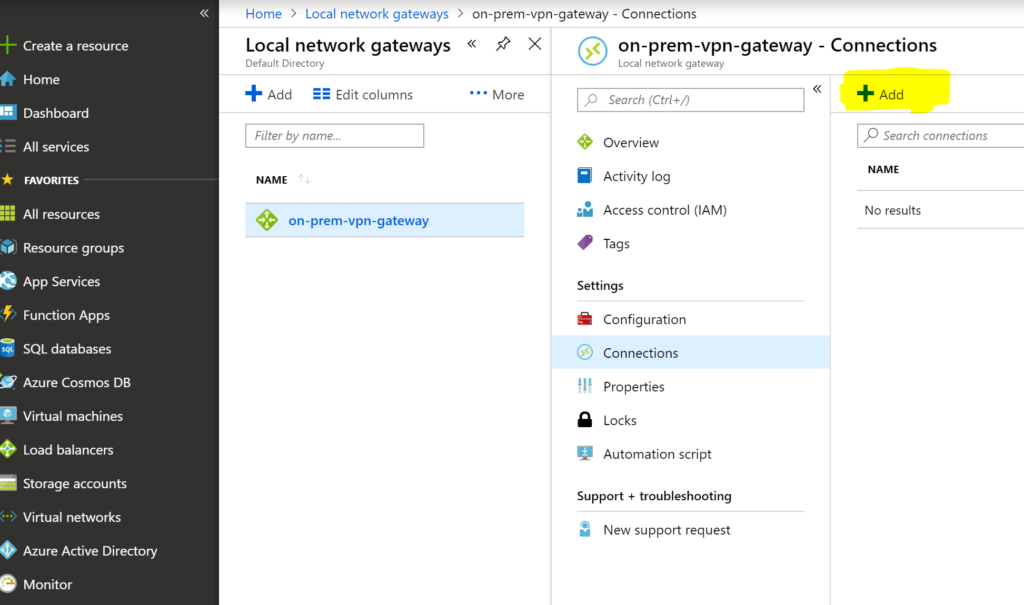
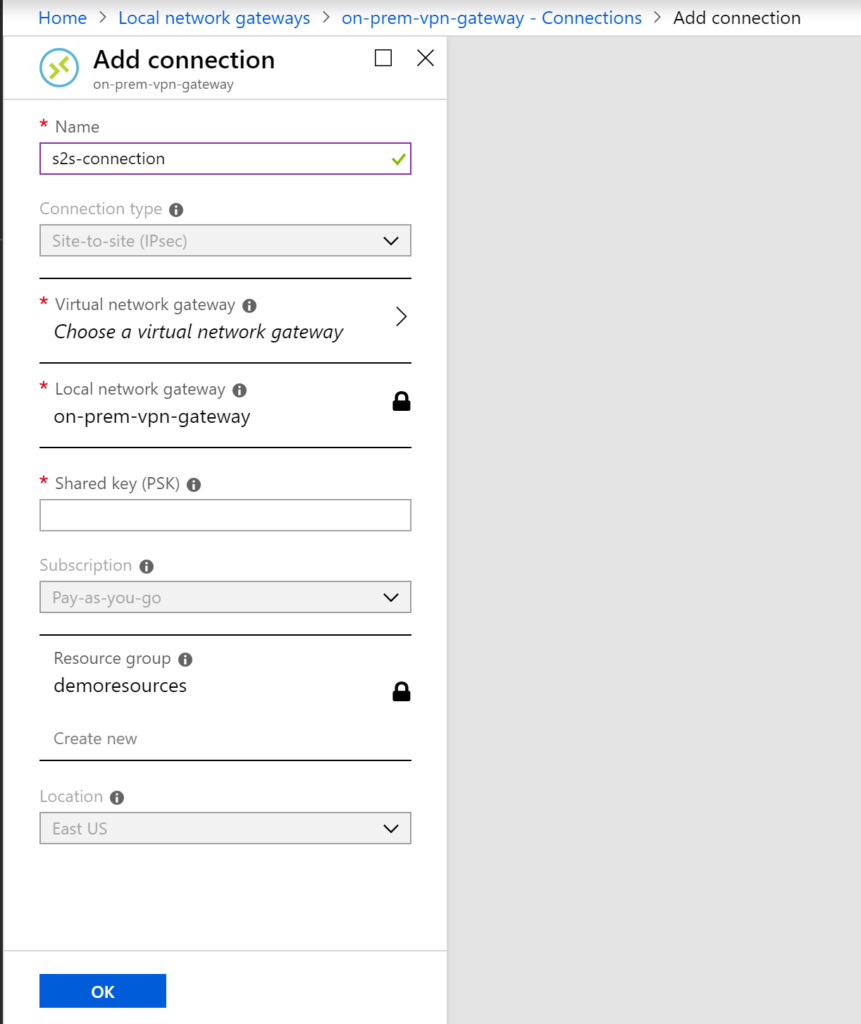
give a name to the connection lets say s2s-connection, connection type is site-to-site , select the virtual network gateway and local network gate-way. Enter the shared key that you have used while creating on-premise network interface and say ok. Once you say ok then it will try to connect to on-premise and status will be shown under connection status column.
At this point you should be able login to VMs on AZURE from on-premise and vice-versa.
If any connection errors occur then it is recommended to use AZURE VPN Diagnostics. More can be read here. and https://azure.microsoft.com/en-ca/services/network-watcher/ this will help you to monitor the information on AZURE VPN gateway and if anything goes wrong then it can write to storage accounts.