Usernames and Passwords are no longer strong enough to protect sensitive information. This post outlines different ways you can protect on-premises and cloud based applications using Microsoft Multi Factor Authentication (MFA). It also explains deployment, configuration options in-depth, API interaction for developers to integrate MFA with existing systems. Additional security never should be a burden for administrators. You can eliminate some admin tasks by enabling self-service options.
AZURE MFA can verify the identity using various methods
- Phone-call – user answers the call and responds with # key
- Text Message – user gets a text message and enters the pass-code in browser to authenticate
- Microsoft Authenticator App – User can download and register this from app-store to iPhone, Android and windows phones. App sends the push-notification to verify your authentication request. This App can also generate a PIN code which is optional.
Configuring Cloud-Application to use MFA
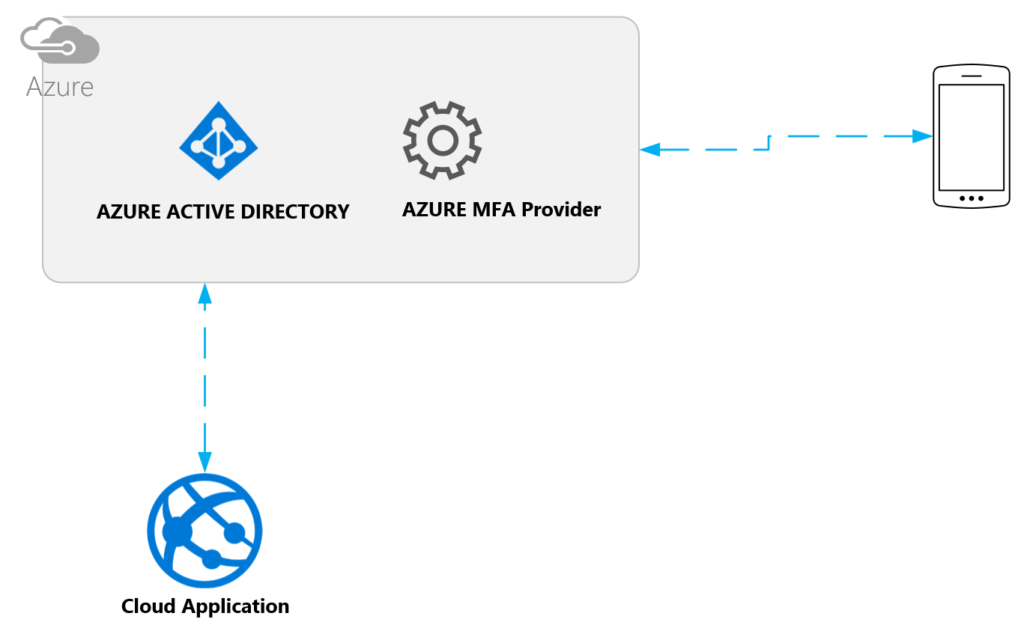
User registers a device with their account. For cloud-based applications this account will be stored in Azure Active Directory.
once the phone is been registered with use identity, user will get an authentication request to phone when logging into the application. Depending on method of user chosen he/she will get authenticated. Any application that you built on top of AZURE AD can leverage multi-factor authentication.
How to enable in AZURE Portal?
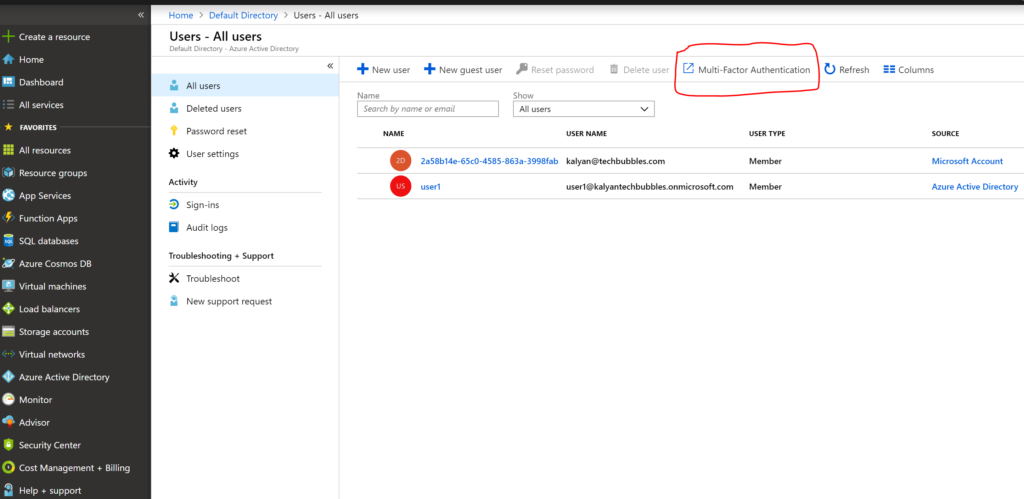
- Login to the AZURE portal and browse AZURE AD users and click multi-factor authentication link shown in following screen
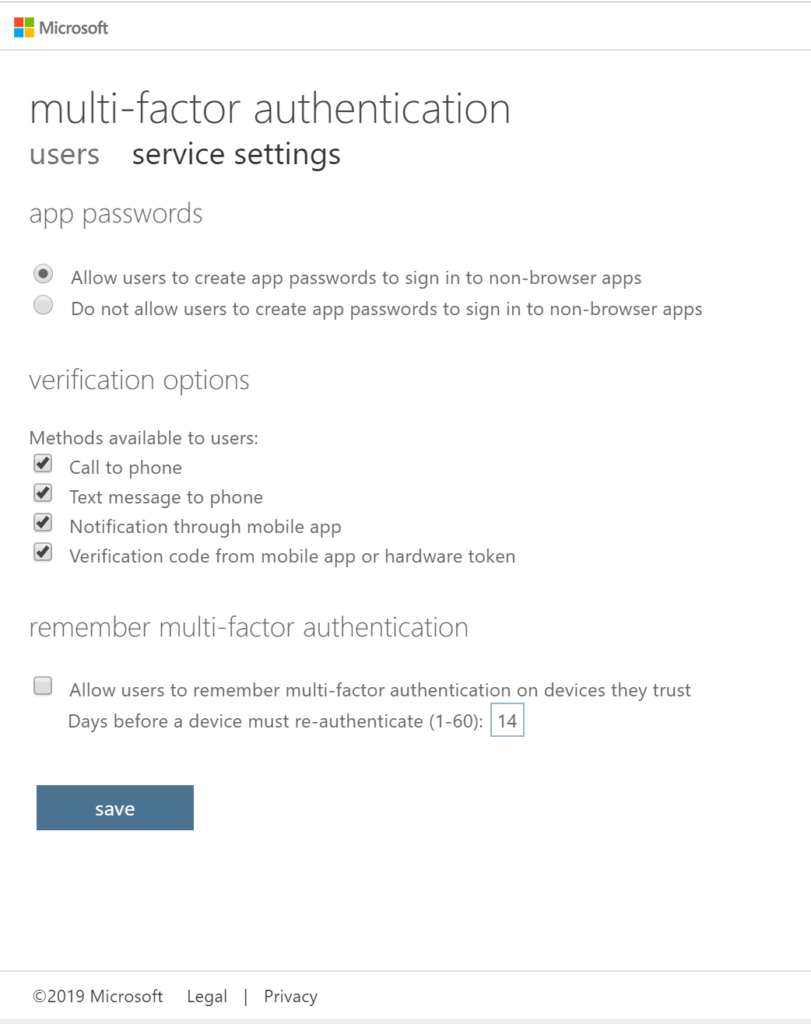
2. It will navigates you to MFA provider screen and prompt to enter credentials again, click service settings and check-all applicable verification methods.
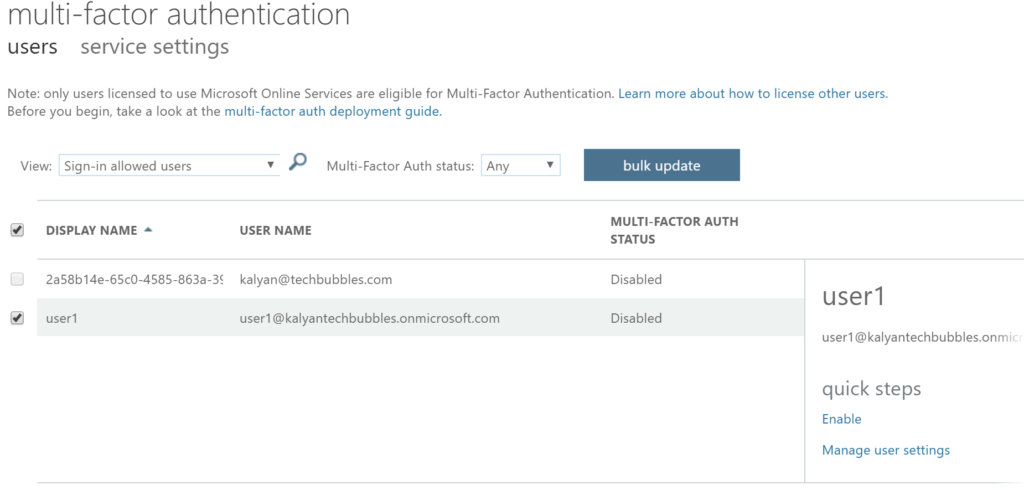
3. Click users link and select the user which you want to enable MFA as shown in following
4. After you enable MFA, First time when user1 tries to login to the application it ask him enter mobile number as shown in following screens

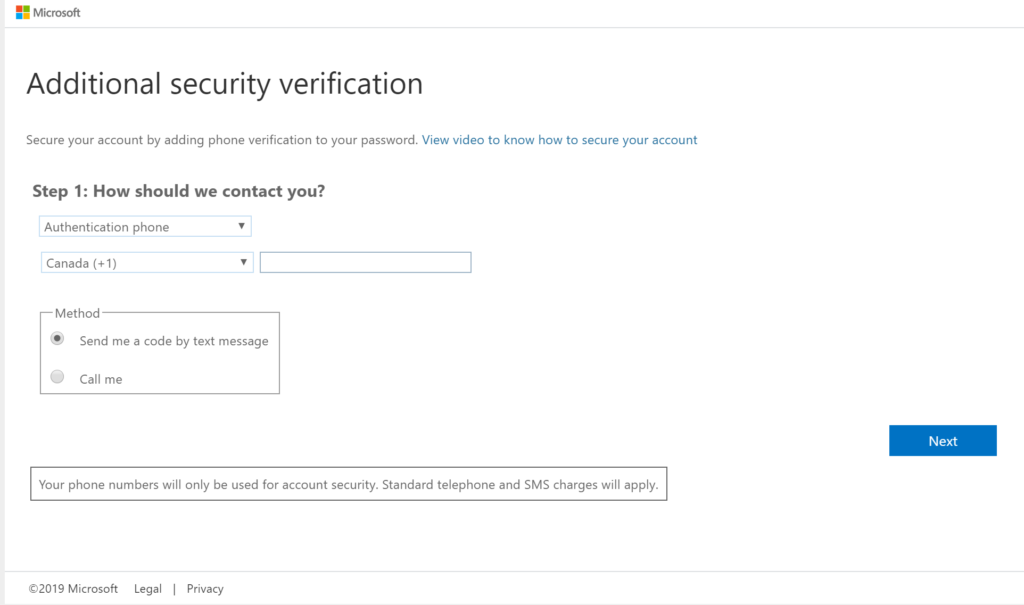
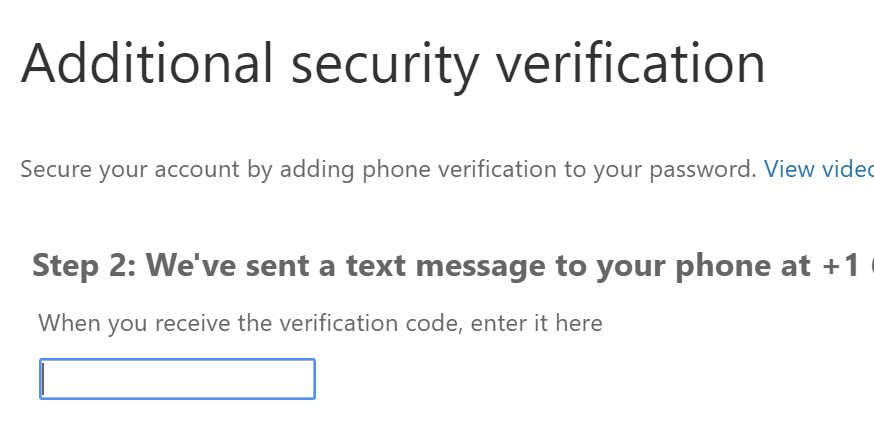
enter the verification sent to your mobile, that’s it user1 configured to use AZURE MFA.
AZURE MFA Additional Features
You need buy license to use following features, customizable voice messages when your user receives a phone-call for authentication, Fraud alerts, Customizable caller ids instead of random phone numbers that you receive these verification calls. Administrator can block/unblock user if he/she forgets or lost the phone. On-premises application integration available with this license. You can create different MFA providers with different charge-back schemes.
Configuring on-premise applications to use MFA
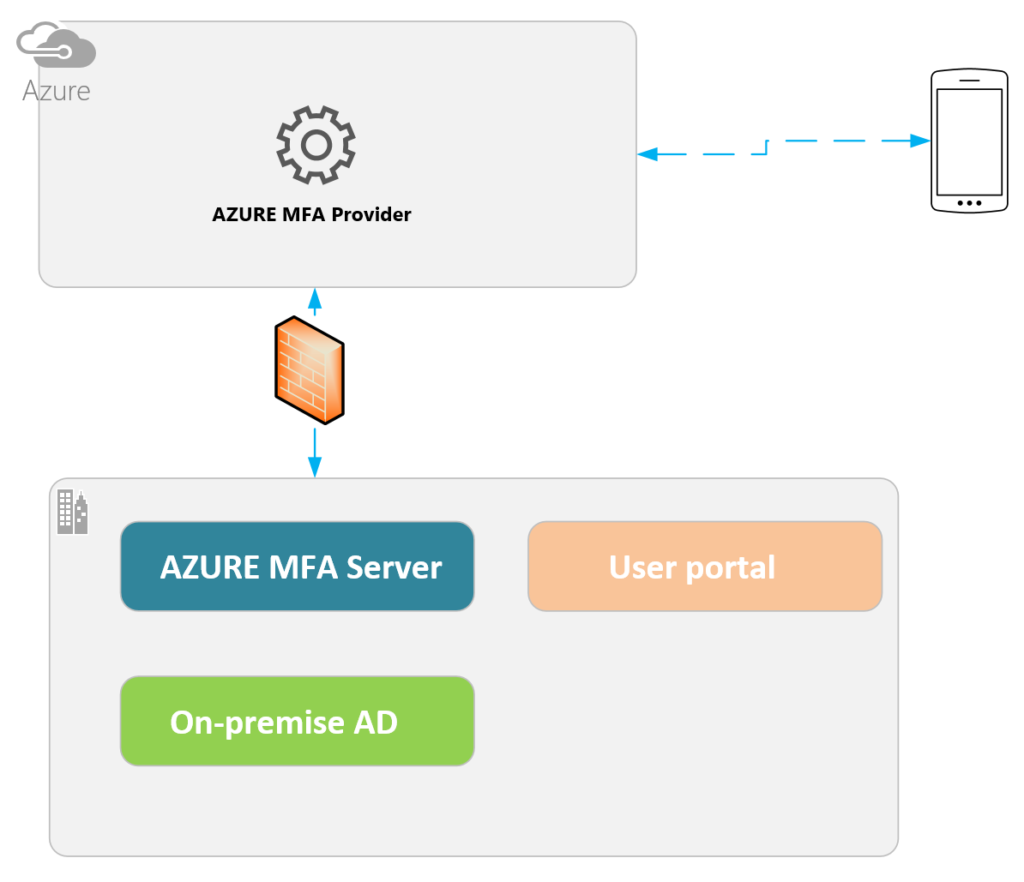
Download and install MFA authentication server in on-premise. The portal has more features as mentioned in the post and looks as follows
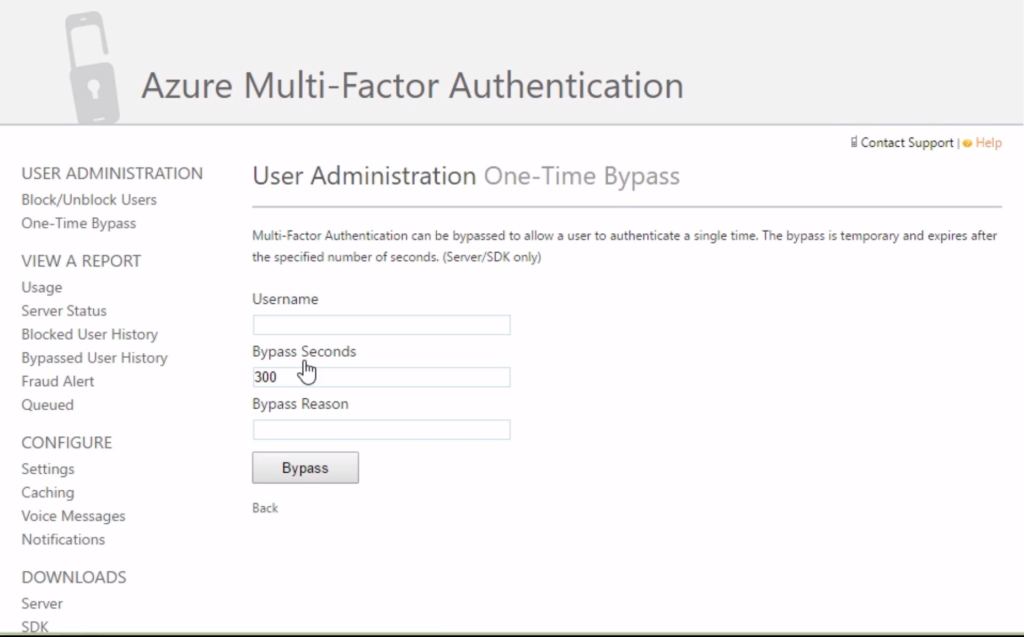
The configuration steps for on-premise authentication server can be read here https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfaserver-deploy
once the installation is complete, you may have to install web services SDK so that you can interact with this server through code.
This is important step in MFA server configuration in on-premise as it communicates to AZURE provider using web-services.